HITRUST

HITRUST CSF is a unifying global framework to manage information risk and safeguard sensitive information for healthcare and other organizations. The HITRUST Approach provides a comprehensive management structure to effectively manage data, information risk, and compliance in a complex and rapidly-changing business environment.
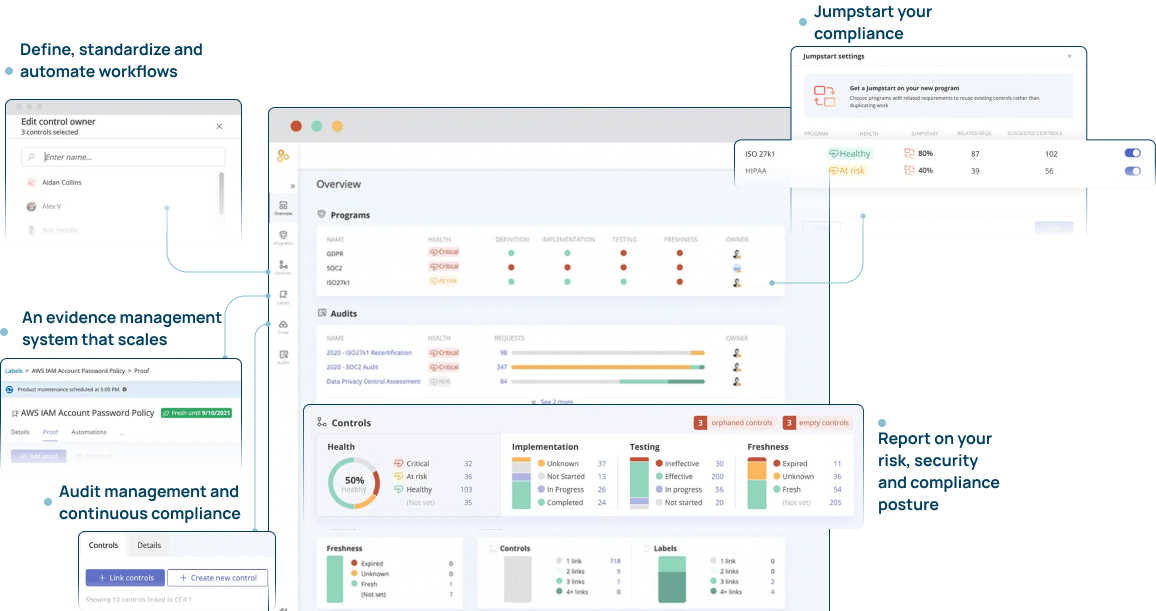
Compliance Management Platform
HITRUST Audit Management and Continuous Compliance by Experts
HITRUST is based on the HITRUST CSF (Common Security Framework), a certifiable framework that results in a scalable, flexible, and efficient approach to regulatory compliance and risk management. The HITRUST CSF leverages nationally and internationally accepted security and privacy-related regulations, standards, and frameworks – including ISO, PCI, NIST, HIPAA, AICPA Trust Service Criteria, and State laws.
About HITRUST
HITRUST History
The HITRUST Alliance was founded in 2007 to develop and promote programs to ensure the security of sensitive information and manage information risk. The HITRUST Alliance created its own standardized framework, enabling any organization to demonstrate compliance and obtain HITRUST certification. HITRUST began as a healthcare-industry centric framework, but has evolved to address the needs of organizations across many industries.
HITRUST Approach
A comprehensive program for information risk management and compliance is delivered in the HITRUST Approach. This fusion of security and compliance mandates combine into an approach that ensures coordination between an organization’s information risk management and compliance objectives. HITRUST refers to this concept as “assess once, report many.”
HITRUST myCSF
The HITRUST CSF (Common Security Framework assessment) can be applied by any organization that generates, accesses, organizes, or transfers sensitive information. The HITRUST CSF is a standard certifiable by security assessors and was created as a risk-based rather than a compliance-based approach to organizational security. The HITRUST CSF Assurance program incorporates features from popular security frameworks including ISO, PCI, NIST, and HIPAA but still allowing for a highly adaptive approach. The HITRUST CSF includes multiple reporting domains and implementation levels, resulting in hundreds of possible control specifications.
CSF Levels of Implementation
HITRUST CSF controls allow for distinct implementation levels, with increasing levels of sophistication. Implementation levels differ depending on the level of risk. The higher the risk, the more restrictive the control. Risk is similarly divided into three categories: organizational, system, and regulatory risks. All three types of risks are considered to determine the appropriate implementation level for a particular control.
HITRUST assessments begin with an extensive scoping evaluation. This process includes understanding the organization, systems, processes, and regulatory requirements for the assessment. Assessment scoping includes identifying specific organizational business units, physical locations, systems, and other elements to be included in the HITRUST CSF assessment. The scope also depends on the resources, security and privacy program maturity, and risk tolerance of the organization. Organizations undergoing a HITRUST CSF validated assessment are also required to prepare a detailed description of the systems and processes included in the assessment.
HITRUST VS. HIPAA


HITRUST expands upon the HIPAA requirement to include additional security and risk management guidelines to form a cohesive framework. HITRUST includes all of the HIPAA safeguards, but is not limited to them. HITRUST and HIPAA are therefore not interchangeable.
The HITRUST framework leverages:
- Control Objectives for Information and Related Technology (COBIT)
- International Organization for Standardization (ISO)
- Federal Trade Commission (FTC)
- Centers for Medicare and Medicaid Services National Institute of Standards and Technology (NIST)
- Payment Card Industry Data Security Standard (PCI DSS)
- Other Federal and State regulations
Framework developed by security and privacy experts to includes aspects of HIPAA
The HITRUST CSF streamlines the validation compliance with HIPAA-mandated security controls
The Health Insurance Portability and Accountability Act, or HIPAA, is a set of standards and regulations created to safeguard sensitive information within the healthcare industry. HIPAA compliance restricts access to patient health information to only the medical professionals, vendors, and other personnel that need it.
The foundation for patient information security and plays a crucial role in data privacy
Includes the Privacy Rule, Security Rule, Enforcement Rule, Omnibus rule (HITECH Act), and the Breach Notification Rule
Operates as a function of law and in general, does not require formal validation assessments
Enforcement actions usually follow known violations, such as a data breach
Requires organizations to adapt to ever-evolving cybersecurity challenges
Does not offer anything other than guidelines to follow
HITRUST does not replace HIPAA compliance or deem an entity as HIPAA compliant. However, it offers measurable benchmarks and goals which make applying administrative, technical, and physical safeguards a simpler task. This factor alone has resulted in HITRUST being considered a highly reliable tool for maintaining security and compliance.
HITRUST CSF Compliance Assessment
The HITRUST CSF Compliance Assessment journey is largely dependent on the scale and complexity of your organization. The project lifecycle has distinct phases:
Phase 1: Readiness Assessment
2 to 6 weeks elapsed timeframe
Phase 2: Remediation
2 to 12 weeks elapsed timeframe
Phase 3: Compliance Assessment and Validation
3 to 6 weeks elapsed timeframe
A HITRUST certification is valid for two years.
HITRUST CSF Compliance Benefits
Scalable and Cost-Effective
Mapped to Federal and State regulations, and multiple industry standards
Shielded by a continually evolving and up-to-date cybersecurity framework
Adaptive risk-based approach facilitates scalability as the organization grows
Universal Cybersecurity Framework
Comprehensive approach to align security and regulatory compliance requirements
Decreases organization’s control variability
Simplifies security and compliance processes
Competitive Advantage
Demonstrates a commitment to a high standard of security
Validates compliance against a tangible and standardized assessment framework
Reduces due-diligence and sales friction with potential customers and partners
HITRUST Services – Need help?
HITRUST certification is a valuable asset for any organization. TrustNet’s expertise and experience with clients across multiple industries, of all sizes, will ensure a successful project.
For more information about HITRUST certification process contact us here.


